BIMI
TL;DR
Brand Indicators for Message Identification (BIMI, pronounced Bih-mee) is an experimental standard to improve brand recognition in email. It allows for email clients to display a verified mark, usually in the form of a brand logo, in the inbox of the user. BIMI can be compared to verified accounts for brands, which are common for social media platforms.
NEW: Mailhardener BIMI asset hosting
Mailhardener now supports hosting BIMI assets (VMC or CMC) directly from your Mailhardener dashboard. Mailhardener BIMI asset hosting takes care of all the technical aspects of BIMI, ensuring your BIMI logo will always work.
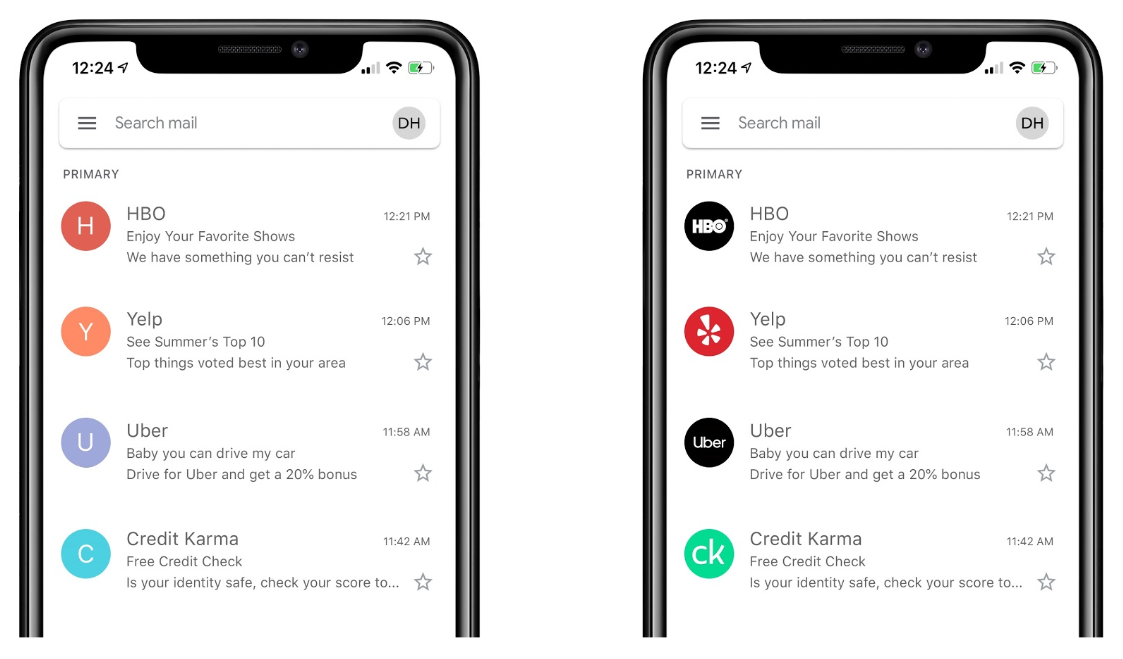
BIMI is aimed at rewarding those who implement DMARC with the opportunity to strengthen their brand presence. The BIMI standard is currently in its eleventh draft, named BIMI-10. The BIMI standard is created and maintained by the AuthIndicators Working Group.
BIMI is still considered experimental, not every email clients supports it.
For the latest developments on BIMI, we also have blog post on the current state of BIMI which we update periodically.
What is BIMI?
BIMI is a mechanism for brands to tie brand identification material, such as logos and trademarks numbers to their domain via a special certificate known as a Mark Certificate (MC). The mark certificate comes in two variants, the Verified Mark Certificate (VMC) and the Common Mark Certificate (CMC), we'll explain the difference between these two later in this article.
If email is received from a domain that implements BIMI, and the email is DMARC aligned, the email client can display the brand indicator and name as found in the mark certificate.
For this to work, the domain must have a DMARC policy of quarantine or reject. When using the quarantine policy, the applied percentage (pct property) cannot be lower than 100%. The Verified Mark certificate must be issued by a certificate authority that is trusted by email providers to supply VMCs.
The BIMI standard is created to drive adoption of DMARC by bigger brands, by rewarding them with stronger brand recognition.
BIMI prerequisites
For BIMI to work, a domain must comply with the following prerequisites:
- The domain must have DMARC implemented with a
quarantineorrejectpolicy. - A certificate with Verified Mark extension must be obtained from a trusted certificate authority.
- A DNS record must be placed which points to the certificate which must be served over an HTTPS scheme.
- Although not strictly required, all email sources that are used for the domain should add the BIMI header to all emails send.
Roughly speaking, BIMI works like this for the receiver:
- An email is received from
domain.com. - The email is checked for DMARC alignment against the DMARC policy as published by the domain.
- The receiving system checks for the existence of a BIMI DNS record at
domain.com, using the selector found in the BIMI email headers. - The receiving system downloads and verifies the Verified Mark certificate (VMC) from the location supplied in the DNS record. The certificate must be from a trusted authority, and match
domain.com. - If all previous steps pass, the SVG brand indicator found in the VMC is displayed as brand indicator in the mailbox of the receiver.
DMARC policy
Displaying a brand indicator in the email client of the receiver comes with the responsibility of verifying that the email is coming from an authorized source. Hence, a 'strong' DMARC policy is a requirement for BIMI to work.
Defined in BIMI-10 section 1, a 'strong' DMARC policy is defined as:
- The sender domain must have DMARC enabled with a
quarantineorrejectpolicy. - If set, the subdomain policy (the
spvalue) must also meet this minimum policy strength. - When using
quarantinepolicy, it must be applied to 100% of the email sent by the domain, thus thepctDMARC value must be set to100or omitted (100% is the default). - When using
rejectpolicy, it is allowed to set thepctproperty lower than 100%.
The following DMARC records are not valid for use with BIMI:
v=DMARC1; p=none;
(policy is not 'quarantine' or 'reject')
v=DMARC1; p=quarantine; pct=25;
(quarantine policy is not applied to 100% of emails)
v=DMARC1; p=reject; sp=none;
(reject policy is not applied to all subdomains)BIMI Mark Certificate
The mark certificate is the source of trust for email clients to safely display a brand indicator in the inbox. It is also the most misunderstood portion of the BIMI standard.
Although the BIMI draft marks the certificate as optional, for BIMI to work with any of the public email systems the BIMI mark certificate is required.
A Mark Certificate is a regular X.509 certificate, as commonly used for securing websites with HTTPS, but with an additional extension for including a logo file (the brand indicator).
In the Mark Certificate extension, the brand indicator (the logo) is stored as an SVG vector image.
The domain name(s) owned by the brand are stored in the subjectAltName of the certificate, an email client will verify the sender domain of the email to the domain specified in the mark certificate.
A BIMI mark certificate can be obtained through a Certificate Authority (CA), just like with web server certificates. There are two types of Mark Certificates offered:
| Type | Name | Proof of mark ownership |
|---|---|---|
| VMC | Verified Mark Certificate | Trademark office |
| CMC | Common Mark Certificate | Website history |
The VMC and CMC are technically identical, the difference lies within the verification process of the CA. The CA may use a different root or intermediary key to sign the certificate.
Verified Mark Certificate
A Verified Mark Certificate (VMC) was originally the only support type of proof of authority for BIMI.
A VMC proofs ownership of a brand, which include the mark (logo), name, address, registration numbers, and the website URL(s).
In order for the CA to verify the ownership of the brand, the brand must be registered at the trademark office representative of the jurisdiction of the brand owner. The CA will collaborate with the local trademark office to verify ownership of the brand. Which trademark office is queried depends on the jurisdiction of the organization owning the brand.
Due to the amount of manual validation and verification required for the CA to issue a VM certificate, only a select few CAs currently offer VM certificates. It is also not expected for VM certificates to be offered at competitive prices compared to HTTPS certificates.
Common Mark Certificate (experimental)
As of September 2024, the BIMI workgroup announced an alternative to the Verified Mark Certificate (VMC) called the Common Mark Certificate (CMC). The CMC is aimed at lowering the barrier to verifying a mark (logo) by removing the trademark office verification and relying on website validation instead. The CMC standard is currently only supported by Google (Gmail / Google Suite).
For a mark to be verified by Google for CMC usage, the logo must be published on the website of the domain, with proof of ownership. The logo must also have been present at least 1 year (12 months), Google is capable of verifying that by using their archives.
As of writing, some CAs have started to offer CMCs, but details of the verification process (and possible automated verification via ACME) are yet to be finalized.
The BIMI DNS record
A DNS TXT type resource record must be published under the email domain. This record points to an SVG vector image of the brand indicator, and a verified mark certificate. Both the SVG image, as the VM-certificate must be served over an HTTPS scheme, with a valid web server certificate.
A domain can have multiple BIMI records (as a domain may serve multiple brands).
Each BIMI record is identified by a selector, the same as how DKIM public keys are identified.
An email sent from the domain may have the BIMI selector value in the headers of the email.
If no header value is present, a default selector with value default may be assumed by the email client.
The location of the BIMI DNS record is [selector]._bimi.[domain], for example:
default._bimi.mailhardener.comThe BIMI DNS record format is the typical key/value format as we know from other email hardening mechanisms such as DKIM and DMARC. The typical BIMI record may look like this:
v=BIMI1; l=https://example.com/logo.svg; a=https://example.com/bimi_cert.pem| Key | Name | Description |
|---|---|---|
v |
Version | Must be the first field in the record, must be set to value BIMI1 |
l |
Location | Optional, points to an SVG format indicator image of the brand, must be served over HTTPS |
a |
Authority Evidence Location | Optional, points to a PEM format VM-certificate, must be served over HTTPS |
avp (previously s=) |
Avatar Preference | Optional, can be brand (default, previously bimi) or personal. If set to personal, mailbox provider should display personal avatar instead of BIMI mark. |
Notes:
- In the first BIMI draft, it was allowed for the
a=value to contain the valueself, this is no longer allowed since draft BIMI-01. - In draft BIMI-08, the avatar preference field used
s=, this was changed in BIMI-09 toavp=. - In draft BIMI-10, the value for the avatar preference field to prefer BIMI over a personal avatar was changed from
bimitobrand.
We want to emphasize once more that although the authority location (a=) value is technically optional, a BIMI mark certificate (VMC or CMC) is required for BIMI to work with public email providers.
You can test a BIMI DNS record for validity using our free to use BIMI record validator tool.
The BIMI email header
An optional (but recommended) header BIMI-Selector should be added to all email sent from the domain to instruct a BIMI-capable email receiver that BIMI is used, and where to find the VM-certificate.
| Key | Name | Description |
|---|---|---|
v |
Version | Must be the first field in the header, must be set to value BIMI1, indicates that BIMI is to be used for the domain |
s |
Selector | Optional, the selector value where the DNS record is located. Defaults to default if omitted |
An example of an email containing a BIMI header:
From: example@mailhardener.com
BIMI-Selector: v=BIMI1; s=demo;
Subject: This demonstrates BIMI
Hi, this is a demo for BIMIFor the example above, a BIMI capable receiver will look for a BIMI DNS record at demo._bimi.mailhardener.com.
If no BIMI header is present in the email, the receiver may still attempt to query a BIMI DNS record at the default selector location.
There are also 2 additional headers BIMI-Location, BIMI-Indicator and BIMI-Logo-Preference (since BIMI-09) which may be injected into the email by the receiving email server as hints to the email client (MUA).
BIMI in practice
As mentioned, BIMI is still an experimental email standard.
Some major email providers, such as Google and Yahoo are currently testing BIMI as part of a pilot program. It is not enabled for all of their customers just yet, meaning that BIMI indicators are not always shown for every user.
A list of trusted issuers of VM-certificates for BIMI is maintained by the AuthIndicators workgroup. The current list is:
- DigiCert
Entrust(discontinued)- GlobalSign
- SSL.com
Mailhardener has a BIMI validation service which sees thousands of validations per day, but it is rare for us to see a domain with an actual VM-certificate set.
We also published a blog post with the current state of BIMI, which we update periodically with the latest updates on BIMI.
Mailhardener has full BIMI monitoring support in the Mailhardener dashboard.
Conclusion
BIMI allows for stronger brand recognition which should reduce fraudulent email and drive the adoption of DMARC.
The BIMI standard is still very much in experimental phase. Few email services have BIMI fully integrated, and only time will tell if other email services adopt the technology.
The Verified Mark Certificates required for BIMI are available from a select group of certificate authorities, but the cost of such VMC may prove too high for smaller brands. The proposed CMC standard has potential to lower this barrier, but adoption has not yet been widespread.
Further reading
Tools
Share your thoughts!
One last thing: If you have questions, comments or thoughts on this article, don't hesitate to shoot us an email.
You can also follow and reach us on X @Mailhardener.